Architecture for AWS VPC: Internet-facing Public subnet with Private subnet backend
Background
This blog post was created with a primary reason to support my AWS Architecture Certification (I passed!) and as a secondary purpose as a future reference. This post will cover the basic design concepts with introductory implementation notes so that the VPC environment can be recreated.
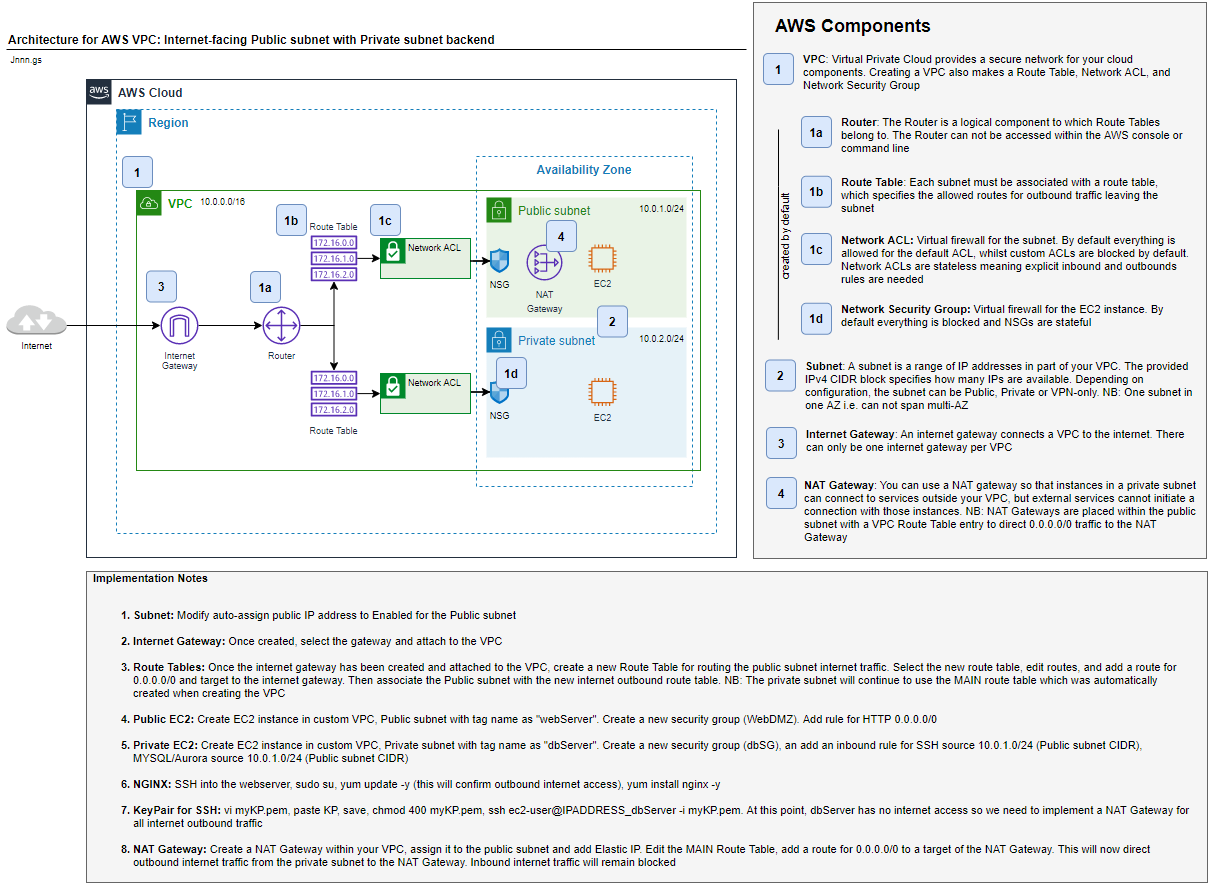
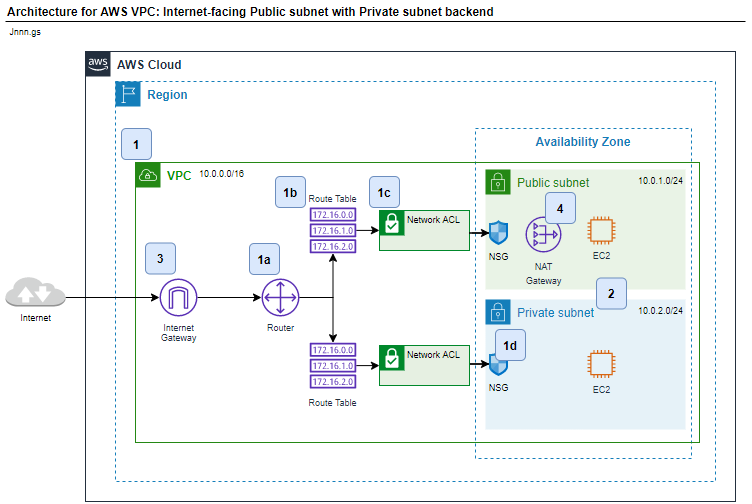
The main system architecture picture at the top of this post has reference numbers against the core components of the VPC, which are used to provide meaningful information about their purpose. At the bottom of this post, I have provided a rich diagram, including all the information needed for a cheat sheet reference diagram.
What is an Amazon Virtual Private Cloud?
An Amazon Virtual Private Cloud (Amazon VPC) is one of the fundamental architectures and part of many "typical" AWS designs. Its implementation covers a lot of best practices and provides a highly secure environment for solutions that require public-facing access with securely protected backends.
System Architecture Reference
- [1] VPC: Virtual Private Cloud provides a secure network for your cloud components. Creating a VPC also makes a Route Table, Network ACL, and Network Security Group. The following components are automatically created as part of the VPC creation.
- [1a] Router: The Router is a logical component to which Route Tables belong to. The Router can not be accessed within the AWS console or command
- [1b] Route Table: Each subnet must be associated with a routeing table, which specifies the allowed routes for outbound traffic leaving the subnet
- [1c] Network ACL: Virtual firewall for the subnet. By default, everything is allowed for the default ACL, whilst custom ACLs are blocked by default. Network ACLs are stateless meaning explicit inbound and outbound rules are needed
- [1d] Network Security Group: Virtual firewall for the EC2 instance. By default, everything is blocked and NSGs are stateful
- [2] Subnet: A subnet is a range of IP addresses in part of your VPC. The provided IPv4 CIDR block specifies how many IPs are available. The subnet can be Public, Private or VPN-only depending on the configuration. NB: One subnet in one AZ i.e. can not span multi-AZ
- [3] Internet Gateway: An internet gateway connects a VPC to the internet. There can only be one internet gateway per VPC
- [4] NAT Gateway: You can use a NAT gateway so that instances in a private subnet can connect to services outside your VPC, but external services cannot initiate a connection with those instances. NB: NAT Gateways are placed within the public subnet with a VPC Route Table entry to direct 0.0.0.0/0 traffic to the NAT Gateway
Implementation Notes
- Subnet: Modify auto-assign public IP address to Enabled for the Public subnet
- Internet Gateway: Once created, select the gateway and attach to the VPC
- Route Tables: Once the internet gateway has been created and attached to the VPC, create a new Route Table for routing the public subnet internet traffic. Select the new route table, edit routes, and add a route for 0.0.0.0/0 and target to the internet gateway. Then associate the Public subnet with the new internet outbound route table. NB: The private subnet will continue to use the MAIN route table which was automatically created when creating the VPC
- Public EC2: Create EC2 instance in custom VPC, Public subnet with tag name as "webServer". Create a new security group (WebDMZ). Add rule for HTTP 0.0.0.0/0
- Private EC2: Create EC2 instance in custom VPC, Private subnet with tag name as "dbServer". Create a new security group (dbSG), an add an inbound rule for SSH source 10.0.1.0/24 (Public subnet CIDR), MYSQL/Aurora source 10.0.1.0/24 (Public subnet CIDR)
- NGINX: SSH into the webserver, sudo su, yum update -y (this will confirm outbound internet access), yum install nginx -y
- KeyPair for SSH: vi myKP.pem, paste KP, save, chmod 400 myKP.pem, ssh ec2-user@IPADDRESS_dbServer -i myKP.pem. At this point, dbServer has no internet access so we need to implement a NAT Gateway for all internet outbound traffic
- NAT Gateway: Create a NAT Gateway within your VPC, assign it to the public subnet and add Elastic IP. Edit the MAIN Route Table, add a route for 0.0.0.0/0 to a target of the NAT Gateway. This will now direct outbound internet traffic from the private subnet to the NAT Gateway. Inbound internet traffic will remain blocked
Cheat-sheet reference diagram